Secure IoT: P2P SSH Setup Guide + Protection Tips
In an era where the Internet of Things (IoT) is rapidly transforming our world, how do we safeguard the myriad of connected devices that underpin our increasingly digital lives, particularly when it comes to remote access and data security? The answer, in a word, is SSH.
The digital landscape has morphed into a complex ecosystem where convenience and efficiency are often at odds with the need for robust security. IoT devices, from smart home appliances to industrial sensors, are now integral to our daily operations. However, their proliferation has simultaneously amplified the potential attack surface for cyber threats. The challenge lies in ensuring that these devices remain seamlessly connected while simultaneously shielding them from malicious actors seeking unauthorized access or data breaches. The importance of maintaining secure connections cannot be overstated. These connections are the digital arteries through which data flows, and their integrity is paramount. The goal is to ensure that the data moving between our devices stays private and out of the wrong hands. This requires the deployment of sophisticated security measures, and in many cases, the use of protocols like Secure Shell (SSH) is a key element.
Let's delve into the core concepts and practical applications of securely connecting remote IoT devices. At the heart of this approach lies the establishment of Point-to-Point (P2P) connections using SSH. This method provides an encrypted channel, allowing you to remotely administer and manage your IoT devices safely and securely. This is particularly relevant for scenarios where direct network access is either impractical or undesirable, such as when dealing with devices deployed in remote locations or behind firewalls. It enables secure remote access, data transfer, and command execution. It's a core piece of the puzzle in a world of increasingly connected objects, and it requires a strategic approach to ensure data integrity and device security.
Before we proceed with the technical details, consider this: The efficacy of your security setup is only as strong as its weakest link. That's why downloading SSH implementations such as OpenSSH from trusted sources is crucial. Always verify the authenticity of any software you install on your systems. Moreover, gaining familiarity with fundamental networking concepts, such as IP addresses, port configurations, and general network setup, is essential for anyone aiming to establish and maintain secure connections. This foundational knowledge will significantly enhance your ability to diagnose and troubleshoot any issues that may arise. The ability to configure these settings properly is fundamental.
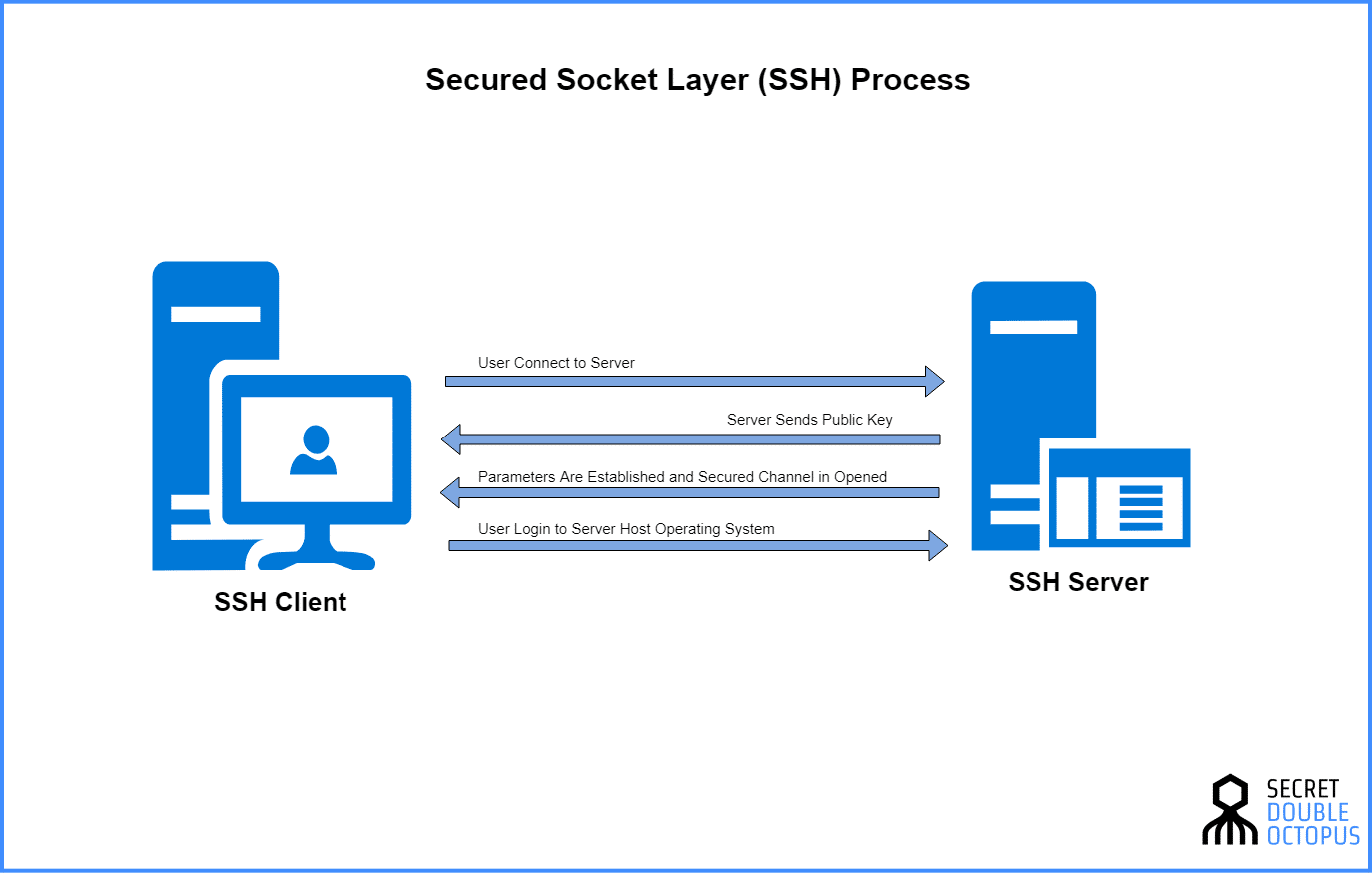
If we are talking about remote IoT device security, it becomes crucial to comprehend the underlying protocols that enable secure connections. SSH is a robust network protocol designed for secure communication over an unsecured network. It uses encryption to protect data transmitted between a client and a server. This is particularly relevant in the context of IoT devices, which often communicate over networks that are vulnerable to eavesdropping and manipulation. SSH ensures that all data exchanged between your remote device and your control point, whether it's configuration updates, data logs, or control commands, is encrypted and protected from prying eyes. The use of strong encryption algorithms helps to ensure confidentiality, integrity, and authentication of the data. It acts as a digital padlock, preventing unauthorized access and securing data as it travels across the network.
To set up a P2P SSH connection, the initial steps involve enabling SSH on the IoT device itself. This typically involves installing an SSH server, like OpenSSH, on the device. Once installed, you'll need to configure the SSH server. This will normally involve specifying the port on which the SSH server will listen for incoming connections, and setting up user accounts. The next step is establishing the P2P tunnel itself. This generally involves the use of a tool like `ssh` on a client machine, using the appropriate options to create a tunnel. The tunnel allows you to securely forward traffic between your client machine and the IoT device. It creates an encrypted channel through which all communications travel, protecting them from unauthorized access. When this is properly implemented, the tunnel acts as a safe passageway for data, guarding it from potential cyber threats.
Now that we know the basic concept and steps, heres a table that can be used with WordPress to create a simple overview:
| Aspect | Details |
|---|---|
| Core Requirement | The IoT device must be capable of running an SSH server (e.g., OpenSSH). |
| Software Source | Download the SSH server software from a trusted and verified source. |
| Network Configuration | Familiarity with IP addresses, ports, and network settings is essential. |
| Connection Type | The primary objective: Setting up a P2P SSH connection. |
| Device Activation | Enable SSH on the IoT device to initiate secure connections. |
| Security Purpose | To protect the devices from cyber threats while maintaining a seamless connection. |
| Data Safeguard | Ensure that data moving between devices stays private and out of unauthorized access. |
| Encryption Protocol | Use protocols like SSH to create encrypted connections. |
| Key Technologies | IP addressing, port forwarding, OpenSSH, and the understanding of network security protocols. |
| Core Function | Securely connect remote IoT devices through P2P SSH. |
The rapid evolution of the digital landscape necessitates a proactive approach to security. As more businesses and individuals integrate IoT technology into their operations, the imperative to safeguard these devices grows in proportion. Securely connecting remote IoT devices becomes paramount, and P2P SSH provides a significant piece of this puzzle. By encrypting the communication channel between your devices, you effectively create a protective barrier against potential cyber threats. This ensures the privacy and integrity of the data that's critical to maintaining seamless and secure connectivity. Your peace of mind increases when you adopt this approach.
The architecture of a secure P2P SSH setup involves several key components. It starts with the IoT device, which acts as an SSH server, listening for incoming connections. This server typically requires configuration to specify the port for listening and to set up user accounts with authentication details. On the other side, a client machine, such as a laptop or desktop, initiates the SSH connection to the IoT device using the established credentials. Between these two points, the SSH protocol encrypts all data traffic. This means that any data transmitted between the client and the IoT device is scrambled into an unreadable format. Even if intercepted, it would be unusable without the proper decryption keys. This security is not merely a feature; it is a necessity.
The core of a secure P2P SSH setup involves encryption algorithms. SSH utilizes robust encryption standards, such as AES and RSA, to encrypt the data in transit. AES (Advanced Encryption Standard) is a symmetric encryption algorithm used for its speed and security. RSA (RivestShamirAdleman) is a public-key cryptosystem used for key exchange and digital signatures. These algorithms provide the essential privacy needed to protect the data as it travels across networks, helping to ensure its integrity and prevent unauthorized access. The use of these encryption methods is fundamental.
Furthermore, the use of SSH keys, rather than passwords, for authentication greatly enhances security. SSH keys employ cryptographic keyspublic and privateto authenticate the user without the need for a password. The public key is placed on the IoT device, while the private key is stored securely on the client machine. When the client machine attempts to connect, the server uses the public key to verify the authenticity of the client. This method drastically reduces the risk of brute-force attacks and keylogging, as passwords are not directly exchanged over the network. Keys offer a significant improvement over passwords, especially in scenarios where security is paramount.
Once the secure tunnel is in place, you can use it for a variety of purposes. One is remote access to the IoT device's command-line interface, which is essential for configuring and managing the device. You can transfer files securely between the client and the device, for example, to update firmware or to retrieve log files. SSH also enables port forwarding, allowing you to access services running on the IoT device as if they were running on your client machine. The versatility of a secure SSH tunnel is remarkable, as it creates secure and reliable pathways for performing many network tasks.
Security is not static; it's a continuous process. Regularly updating the SSH server software and other security packages on the IoT device is vital. These updates often contain patches for newly discovered vulnerabilities. Maintaining strong passwords or using SSH keys for authentication is also crucial. Moreover, periodically reviewing and auditing your security settings is critical. This means verifying that the SSH server is configured correctly, that the ports are appropriately secured, and that the authentication mechanisms are secure. Being proactive about these measures is the cornerstone of a solid security strategy.
Security best practices are often a combination of practical steps and awareness of evolving threats. Implementing these best practices significantly improves the overall security of your IoT setup. This includes limiting SSH access to authorized users, disabling unnecessary services, and monitoring for suspicious activity. Keeping a close eye on network logs and access attempts can alert you to potential security breaches. Finally, stay informed about the latest security threats and best practices by following reputable security blogs, forums, and professional publications. The digital landscape is constantly shifting, and remaining informed is essential for maintaining a robust security posture. This constant state of alertness is part of any well-crafted strategy.
In summary, securely connecting remote IoT devices through P2P SSH is a critical aspect of modern network management. It involves a combination of technical know-how, a commitment to secure practices, and an understanding of how to deal with constantly evolving cyber threats. By implementing P2P SSH connections correctly and adopting a proactive approach to security, you can protect your devices, safeguard your data, and maintain peace of mind. The goal is to navigate the digital world confidently, knowing your devices and data are well-protected.